
We’ve seen a lot of attacks against Bluetooth and BLE over the last few years. Some are attacks against specific Bluetooth stacks with flawed implementations, while other attacks vulnerabilities in the Bluetooth specification and protocol itself.
We typically categorize vulnerabilities in a few levels depending on how broad the impact is:
- Product Vulnerabilities – These are product specific issues and typically result from not understanding or misusing or failing to use the Bluetooth stack properly
- Vendor Stack Vulnerabilities – flaws in this category will tend to impact all customers of a specific vendors, which means there could be thousands of products affected
- Bluetooth Specification Vulnerabilities – This is the broadest category and usually the rarest. The issues in the Bluetooth specification itself will impact all vendors and large swaths of Bluetooth devices. For example, the Key Exchange vulnerability of Bluetooth 4.0 and Bluetooth 4.1 impacts every single device using those specifications
One of the challenges for Bluetooth devices is that there are billions of devices in a wide spectrum, and many don’t have any firmware upgrade capability. From computers running Windows and Linux that can easily get updates, to embedded like headsets where the only firmware the device will ever have is the firmware is the one it left the factory with.
To give us a better understanding of the landscape of Bluetooth security, we’ve compiled data about all the vulnerabilities found in 2023.
Vulnerability Breakdown and CVEs
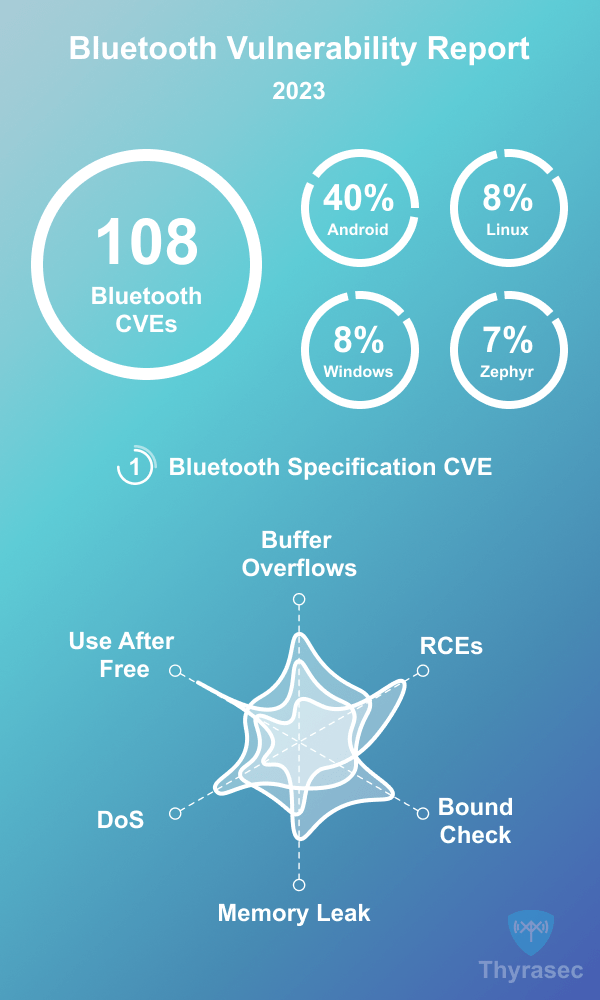
Here’s the breakdown of the top Bluetooth vulnerabilities that were reported in 2023:
| Vendor/Stack | Vulnerabilities | Percentage |
| Bluetooth Specification | 1 | 0.9% |
| Product Specific | 4 | 3.7% |
| Windows | 9 | 8.3% |
| Linux/BlueZ | 9 | 8.3% |
| Android | 43 | 39.8% |
| Zephyr | 7 | 6.5% |
| Silicon Labs | 4 | 3.7% |
| MediaTek | 6 | 5.6% |
| VMWare | 3 | 2.8% |
| Samsung | 3 | 2.8% |
| Qualcomm | 4 | 3.7% |
| Apple | 3 | 2.8% |
| LG Electronics | 1 | 0.9% |
| Huawei | 6 | 5.6% |
| Other | 5 | 4.6% |
There’s a lot of nuance with CVE vulnerability data. First of all, only issues that are publicly reported and assigned a CVE are counted above. These tend to be serious issues. But there can be problems that haven’t been reported (for various reasons), and we won’t be able to count them. Sometimes vendors keep things quiet because the exploit is trivial and they quietly patch the devices. Or maybe they believe that given the inability to patch, disclosure only puts people at risk.
Android Bluetooth Vulnerabilities Dominate in 2023

It’s clear from the data that Android has had a pretty bad year as far as Bluetooth CVEs, with 40% of total Bluetooth vulnerabilities reported being Android. Many of these issues are buffer overflows, but there are Remote Code Execution (RCEs), memory corruption and other problems.
It’s likely someone at Google decided to clean house, review code and found these issues which is why there’s so many. Most of the Android CVEs appear to be internal reports – there’s no security researcher mentioned or a thank you to someone outside of Google as we’d typically expect. Essentially Google is self reporting vulnerabilities.
Many of these seem to be fixed in Android 14, and given how significant of an issue some of these are, unless older versions of Android are patched, early Android are vulnerable.
Other System CVEs
Linux and Windows had 9 vulnerabilities disclosed each, followed by Zephyr (the IoT RTOS used for Nordic and other chipsets) with 7 CVEs. It’s pretty clear no system escapes from vulnerabilities, whether closed or open source.
Of the chipset vendors, MediaTek had the most issues, but Qualcomm and Silicon Labs figure as well. Vulnerabilities in Vendor stacks affect a huge swatch of products, because they’re impact every product using that version of the Bluetooth stack.
Product Specific Bluetooth Vulnerabilities
Speaking of that, Product Specific issues, which are CVEs that we categorize as impacting essentially one particular product from a manufacturer, was at only 4 CVEs. 2023 was another year where more issues were found in stacks and systems than in products.
This isn’t that unusual. Finding flaws in products requires access to the product itself. Even with the product, there’s a lot of effort to extract the firmware and reverse engineer it. If that’s something you’re looking to do, then we have a great guide to extracting firmware.
Meanwhile, Android, Linux and other Bluetooth stacks are available online. The code is ready for inspection in github or online repositories. The code can be analyzed through a variety of tools. This makes finding vulnerabilities much easier.
You should remember that simply finding more vulnerabilities, while on the surface appears to imply that a stack is more vulnerable, fails to consider the fact that closed stacks are also likely vulnerable.
Bluetooth Specification
As far as the Bluetooth Specification itself, one vulnerability was released this year and we’ve covered it in our Top Bluetooth Vulnerabilities guide.
The BLUFFS attack uses the previously disclosed KNOB attack to compromise future sessions, something that had not been done before in Bluetooth attacks.
But, because the attack relies on the same concept as KNOB, the mitigation is the same – to ensure that the key size used for the connection is large, ideally 7 bytes or larger.
BLE Flipper Zero Spam Attack

Though not a vulnerability per se with an assigned CVE, there’s been several attacks in the real world using the Flipper Zero that cause Bluetooth smartphones to crash, among other things. capable devices caused quite a bit of disruption in the real world in 2023.
The issue comes down to simplicity vs security – Apple, Google, and device manufacturers like to give end users the ability to connect to their newly bought devices quickly. They did this by creating specific advertising packets in Bluetooth that iOS and Android devices can find, avoiding the user having to manually scan via Bluetooth.
Well, developers can replicate these packets in the Flipper Zero and send a massive amount of them. Apple and Google didn’t seem to consider this possibility since the flood of notifications caused devices to crash.
Luckily the latest versions of Android and iOS guard against this issue (but can’t resolve it fully since the advertising packets are needed)
BLUFFS Attack – CVE-2023-24023
The BLUFFS attack – Bluetooth Forward and Future Secrecy Attacks and Defenses is the Bluetooth protocol vulnerability released in 2023. It leveraged the key negotiation attack (KNOB) previously discovered against Bluetooth but took it further – once the attack is done, it compromises future connections.
References
BLUFFS: Bluetooth Forward and Future Secrecy Attacks and Defenses